2016 update: Turns out this is the most popular article on this site – with nearly 4 years of changes to Google Chrome since it was posted, the instructions needed a little tweaking..!
Brightcove typically delivers videos via a flash stream – making it almost impossible to download (as it is a stream, there is no file to save). A video capture of the stream might be possible, but there’s an easier way if the video has a .mp4 “fallback option” for iDevices.
Ingredients
- Video that you want, delivered using a Brightcove stream
- Google Chrome (tested with version 50.0.2661.102)
Recipe
First, you need to disable the Flash plugin in Google Chrome: open Google Chrome, go to chrome://plugins/ and one of the first plugins you should see listed is Flash. Click the Disable link and it ought to go grey.
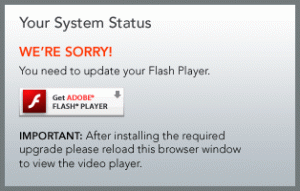
Open a new tab and go to the web address for the video – you should see this:
If the video starts playing instead of seeing the image above, you haven’t disabled Flash properly – try the above steps again.
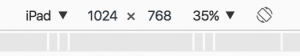
Open the View menu, select Developer and then select Developer Tools. Ensure the user agent dropdown at the top of the page shows “iPad”:
Reload the web page and a video ought to display, with a play icon overlay – that’s the video in .mp4 format. In the Developer Tools section below the website, select the Network tab, then type “mp4” in to the Filter search box. There should be a single item listed in the section at the bottom of the page – this is the video file. Right-click the filename and copy the link address.
Finally, load the copied link address in to the address bar of Google Chrome and load it – et voilà, the video should start playing. Right-click the video and save it to a file.