With a full UniFi network setup (a UniFi USG router, switches, access points and so on), the UniFi router is separate from any modem needed to connect to the Internet. Your setup might look a little like this:
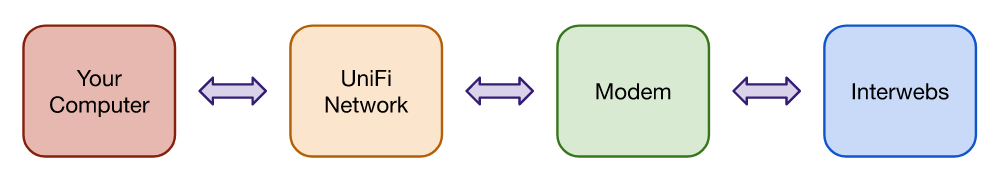
Because your computer isn’t directly connected to the modem, the modem is effectively “hidden” by the UniFi USG. You can still get online, but you can’t see your connection statistics and logs.
Here’s how to fix it:
Pre-requisites
First thing’s first, you need to know the IP address of your modem, and the network range for the UniFi network. The IP address of the modem must also be different to the UniFi network range. In my case, the modem IP address is 192.168.0.1 and the UniFi network range is 192.168.1.0/24.
So the instructions below will work, enter your modem IP address, the network mask in CIDR notation (without the /), enter an unused firewall rule index (the example is probably fine for a USG, but may not be for other Ubiquiti devices), and finally choose the port your modem is connected to.
Once complete, click Update:
Configuration
The remaining steps assume you have a UniFi Network Controller online somewhere, and in that controller you have Advanced Features turned on.
Log into the controller, navigate to the site where your UniFi USG is configured and go to Settings. At the bottom of the screen is the Device Authentication section – copy the SSH authentication details, then SSH into the IP address of the UniFi USG.
Enter the following commands, one line at a time:
configure
set interfaces pseudo-ethernet pREPLACEME4 link REPLACEME4
set interfaces pseudo-ethernet pREPLACEME4 address REPLACEME1/REPLACEME2
set interfaces pseudo-ethernet pREPLACEME4 description "Access to modem"
set service nat rule REPLACEME3 type masquerade
set service nat rule REPLACEME3 destination address REPLACEME0
set service nat rule REPLACEME3 outbound-interface pREPLACEME4
commit
save
exitYou should now be able to access your modem’s status page at http://REPLACEME0/.
Assuming that worked, you need to make the changes permanent with a configuration file for your UniFi Network Controller. Save the following into a text file called config.gateway.json:
{
"interfaces": {
"pseudo-ethernet": {
"pREPLACEME4": {
"address": ["REPLACEME1/REPLACEME2"],
"description": "Access to modem",
"link": ["REPLACEME4"]
}
}
},
"service": {
"nat": {
"rule": {
"REPLACEME3": {
"destination": {
"address": ["REPLACEME0"]
},
"outbound-interface": ["pREPLACEME4"],
"type": "masquerade"
}
}
}
}
}Upload this file into the UniFi Network Controller. The directory you need to upload to will depend on which site you’re configuring; the UI support article for this topic is quite detailed and I’d recommend reading it.
TL;DR: I uploaded mine to /unifi/data/sites/default/ – but read the support article for yourself; don’t assume this is the correct directory for your Network Controller!
Extra: NBN modems
For readers from Australia – there are a few things to know about the modems (or NCD / NTDs) supplied by NBNCo. Some you can access, some you can’t:
| NBN Connection Type | Access to modem? |
|---|---|
| FTTP | n/a |
| HFC | Yes* |
| FTTC | No |
| FTTN/FTTB | Yes |
The two other connection types (Fixed Wireless and Satellite) I have no idea about, so I haven’t included them in this table.
HFC
For HFC, the modem makes it difficult to access the connection statistics page. Thankfully, it’s fairly easy to get in – follow the instructions above (the modem IP is 192.168.0.1), then hard reset the modem by inserting a pin in the reset hole for around 10 seconds.
The reset is complete when the green lights go out and a blue light flashes a couple times – once you see that, release the pin and load http://192.168.0.1/main.html in a browser. Chances are very good you’ll need to refresh several times before the status page displays.
If the modem restarts for any reason (power outage, NBN outage etc), you’ll need to do another hard reset to get back in.
FTTN/FTTB
For these connection types, you supply your own modem – no special instructions required. :) Refer to your modem’s documentation to understand what the default IP address and access details are.
References
I found the following sites helpful in writing this post:
https://owennelson.co.uk/accessing-a-modem-through-a-ubiquiti-usg/
https://forums.whirlpool.net.au/archive/90ym1z23


